Twitter Fails to Uphold the Social Media Contract
In 1651, Thomas Hobbes published his definition of the the Social Contract Theory in Leviathan. In short, Hobbes wrote that men in the State of Nature possess all freedoms, but that will lead to men fighting with each other and killing each other over land and food. Men give up a degree of their freedom to enter into a Social Contract with a government and in return get protection. Jean Jacques Rousseau and John Locke went a bit further and said that a government exists to support the popular sovereignty of the people, there was a couple Revolutions in late 1700s, and not longer the Declaration of Independence was signed. But that’s history, so let’s focus on the present…
If you apply this theory to Social Media, you get the Social Media Contract Theory, which is pretty much the same concept. If people were out on a free-for-all internet they would end up destroying their personal images on websites like MySpace. Therefore, they give up a degree of their freedom to join private social networking sites such as Facebook and Twitter and in return their account and personal information gets protected.
In Twitter’s case, I disagree. Twitter is downright failing to protect their users. In the past two evenings, I have received a Direct-Message from two separate people that I am following that contains a curiosity-inducing message followed by a shortened link through bit.ly:
![]()
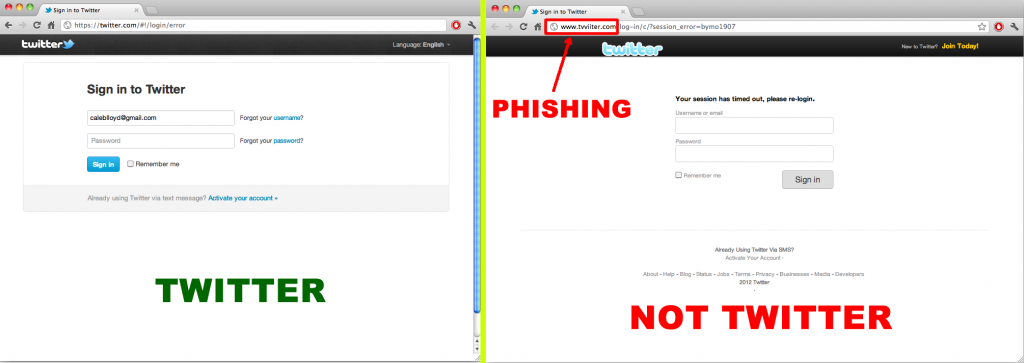
This link takes you to a Phising site:
How the 2012 Twitter Direct Message Virus (phishing scam) Works
From what I have been able to gather about the 2012 Twitter Direct Message Virus, it is a Phishing scam that collects your username and password when you login to the fake-login page. From there, it stores your username and password. Within a short period of time, another script, either on a server run by the Virus owner, or more likely by a server hijacked by a different Virus, the Direct Message Virus automatically logs into your Twitter account. It sends all of your followers a Direct Message (see above) with a curiosity-inducing message body and then a link to the fake Twitter Page (also see above). If one of your followers falls for the phishing scam and enters their Twitter username and password on the fake site, the virus will start the whole process over with their account. What’s even more concerning is that many people use the same Username and Password combination on other websites, meaning those are now vulnerable to attacks as well.
In my opinion, Twitter has created an environment which has increased their users base’s likeliness for falling for Phishing attacks. Additionally, their Direct Message security is apparently non-existant. Here’s my opinion on the matter:
Twitter made URL Shortening Seem Normal
Twitter was originally created as a service to which you could tweet from a 160-character SMS from your cell phone, and has always enforced the 160-character limit in tweets. As a result of this, URL Shortening became extremely popular. Sites like bit.ly, t.co, tinyurl, and even Google’s version goo.gl (not to mention countless more) have popped up all over the place. People are clicking on links with no idea where the link will end up taking them!
In the pre-Twitter days if I clicked on a link and it went through a series of redirects, I would be extremely wary and check extra hard for a phishing site. However, with Twitter, I let my guard down because virtually every link that I click on is a shortened URL that goes through a series of redirects. Twitter has made their user base OK with shortened links that redirect to who-knows-where-until-I-click-the-link, but does not take enough steps to verify that these links are not Phishing sites.
Twitter (apparently) Does Not Scan Shortened URL Endpoints for Viruses
Twitter could take some easy steps to safeguard their users. Fist of all, it is very uncommon for a Twitter user to go down their entire list of followers and send them all a direct message that contains a URL with the same Endpoint (meaning same website once URL Shortening redirects occur). Twitter’s servers should follow shortened URLs, save their endpoints in a database, and do comparisons on URL endpoints. Once a certain number of users send out a lot of direct messages with the same URL Endpoint, a Twitter techie should go check out what’s at that URL Endpoint to see if it’s a Phishing site. I’m positive the algorithm could be perfected to catch more Phishing sites than not. I’m also positive that Facebook already does something like this due to the lack of Phishing that occurs on Facebook.
Twitter (apparently) Does Not Block IP Addresses that Log In to Many Accounts in a Short Period of Time
I cannot say this with complete certainty, but I am willing to bet that the part of the Virus that logs into Twitter and messages your entire follower list occurs from the same server(s) over and over again. Twitter could easily track if a single IP address is logging into many different Twitter accounts in a short period of time. I understand that shared IP addresses for offices and home networks could raise false flags, so let’s take it a step further: place a metric that counts when a single IP Address logs into multiple Twitter accounts AND sends many direct messages containing the same URL Endpoint. It’s a double play- Phishing site identified AND virus server identified!
Twitter Fails to Uphold the Social Media Contract
Twitter, I am calling you out on failing your users. You are not providing a competent degree of security to your users. This needs to be fixed, and I have displayed two simple Algorithms that would not take many resources to implement and would save your users from dealing with the pain of Phishing attacks.